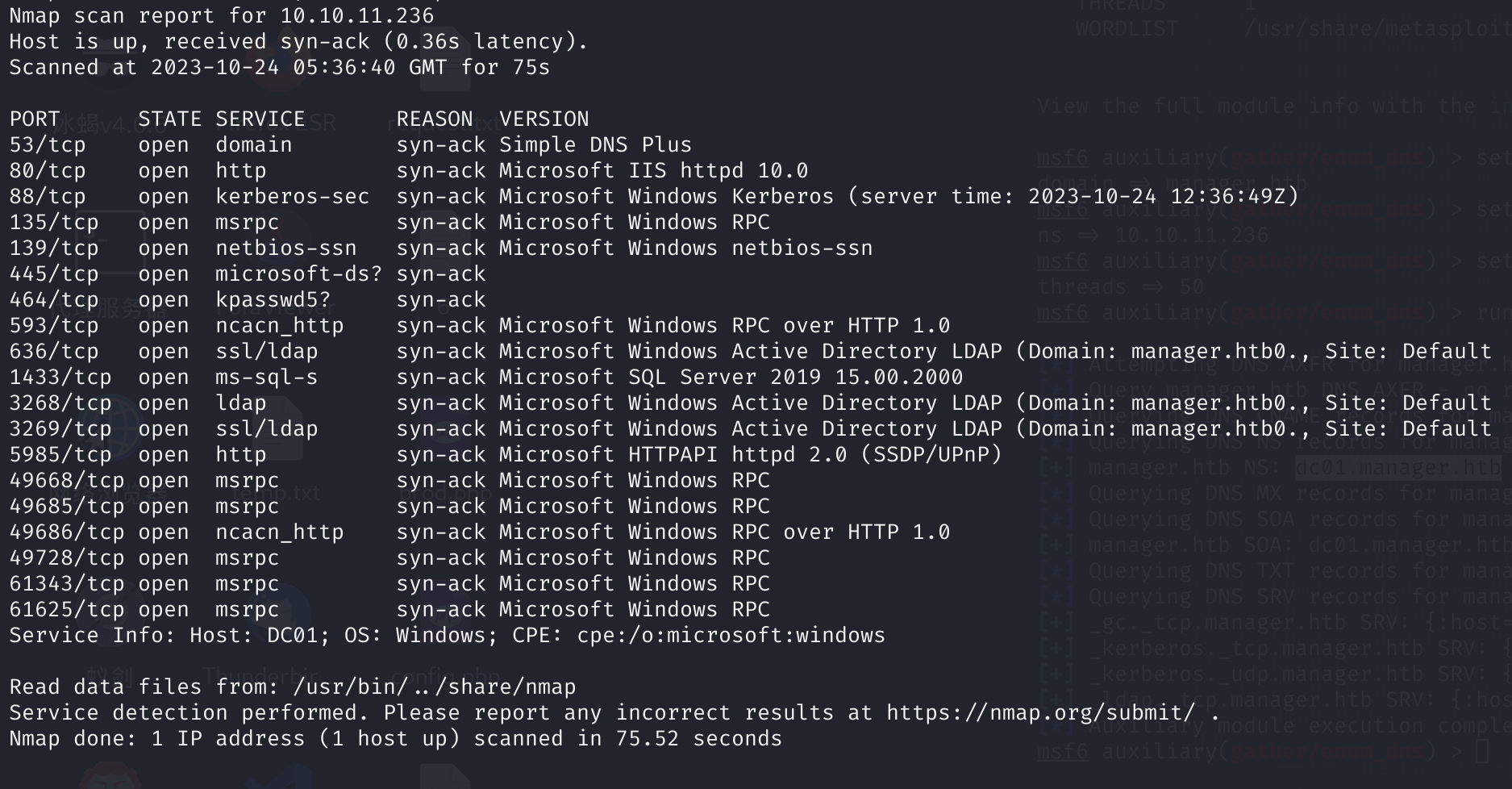
记一次逆向还原AES加密的DB-PASSWORD
HackTheBox RenderQuest WriteUP
HackTheBox Obscure WriteUP
题目
An attacker has found a vulnerability in our web server that allows arbitrary PHP file upload in our Apache server. Suchlike, the hacker has uploaded a what seems to be like an obfuscated shell (support.php). We monitor our network 24/7 and generate logs from tcpdump (we provided the log file for the period of two minutes before we terminated the HTTP service for investigation), however, we need your help in analyzing and identifying commands the attacker wrote to understand what was compromised.
HackTheBox BabyEncryption WriteUp
题目
You are after an organised crime group which is responsible for the illegal weapon market in your country. As a secret agent, you have infiltrated the group enough to be included in meetings with clients. During the last negotiation, you found one of the confidential messages for the customer. It contains crucial information about the delivery. Do you think you can decrypt it?
HackTheBox TwoDots horror WriteUP
HackTheBox breaking grad WriteUP
题目
You and your buddy corrected the math in your physics teacher’s paper on the decay of highly excited massive string states in the footnote of a renowned publication. He’s just failed your thesis out of spite, for making a fool out of him in the university’s research symposium. Now you can’t graduate, unless you can do something about it… 🤷
HackTheBox C.O.P WriteUP
HackTheBox Diogenes' Rage WriteUP
题目
Having missed the flight as you walk down the street, a wild vending machine appears in your way. You check your pocket and there it is, yet another half torn voucher coupon to feed to the consumerism. You start wondering why should you buy things that you don’t like with the money you don’t have for the people you don’t like. You’re Jack’s raging bile duct.